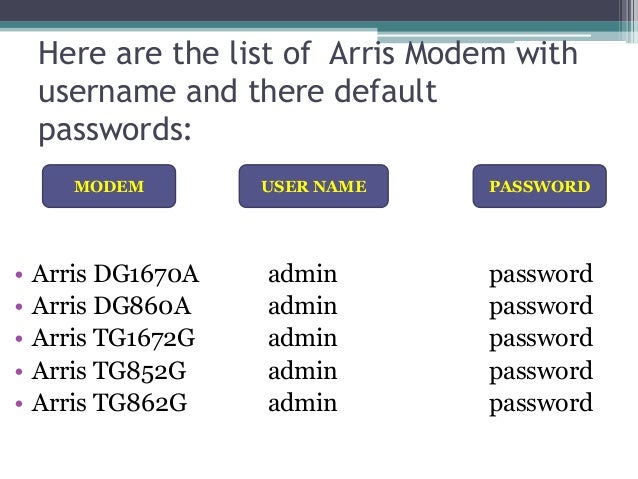
Before joining Arris Partners, Brian led another search firm and several successful high-tech companies. His dynamic style and ability to form solid business alliances has uniquely qualified him to lead Arris Partners. Brian specializes in placing top-tier senior-level and mid-level professionals in world-class companies. ARRIS SURFboard AC1750 SVG2482AC is the first retail Wi-Fi modem-router combo to feature the RDK-B technology. This modem-router combo has the ability to attain very high speeds. It features Wi-Fi speeds of up to 1750 Mbps and download speeds of up to 1 Gbps. Hardware: 12 Months (from date of shipment). 30 to 45-day turnaround from date defective unit arrives at ARRIS. Software: 90 days (from download). E-mail support for software defects only. 2 business day response to e-mail. Maintenance and emergency releases. (Customer-installable fixes and updates to operational software. ARRIS SURFboard SB8200 DOCSIS 3.1 Gigabit Cable Modem, Approved for Cox, Xfinity, Spectrum & others, White, Max Internet Speed Plan 2000 Mbps 4.5 out of 5 stars 22,138 $147.04 $ 147. 04 $199.99 $199.99.
Security researchers have found five gaping holes in the firmware running on Arris modems, three of which are hardcoded backdoor accounts.
An attacker could use any of these three accounts to access and take over the device with elevated privileges — even root — install new firmware, and ensnare the modem in a larger botnet.

The vulnerabilities came to light after a review of the Arris firmware carried out by experts from Nomotion Labs.
According to Nomotion, the flaws are found in both the standard Arris firmware, but also in the extra code added on top by OEMs. In their research, experts looked at an Arris modem installed on the network of AT&T.
Researchers said the flaws affect NVG589 and NVG599 modems. Both models aren't available through the Arris website and appear to be discontinued products. Based on Censys and Shodan data, researchers believe there are at least 220,000 of these vulnerable modems connected online.
Arris Sn Lookup
Below is a summary of all the flaws researchers discovered:
Backdoor #1
Modems come with SSH enabled by default and exposed to external connections. Attackers could use the default 'remotessh/5SaP9I26' username and password combo to authenticate on any modem with root access — this means an attacker can do whatever he wants on the device.

Researchers said they only identified around 15,000 Arris modems featuring this backdoor, meaning ISPs or OEMs most likely blocked external SSH access to most devices.
Backdoor #2
Arris modems come with a built-in web server that runs its internal admin panel. Attackers can authenticate on port 49955 with the username 'tech' and an empty password.
Command injection
The same built-in web server is vulnerable to a command injection flaw that allows attackers to run shell commands in the context of the web server — which is pretty high since the server is used to manage the device via a web panel.
Nomotion says there are over 220,000 devices vulnerable to this flaw. This flaw can be exploited even without the use of one of the hardcoded backdoors. All the attacker needs is to a malformed network request to the modem's 49955 port. Basic ISP-level filters could stop the exploitation of this bug.
Backdoor #3
Attackers can use the 'bdctest/bdctest' username and password to authenticate on the device via port 61001. Exploiting this flaw requires the attacker to know the device's serial number.
Even if not easy to exploit, a determined attacker can find a way to leak the serial number on a per-device basis and access the device. Researchers said this account reveals information about logs, modem's WiFi credentials, and the MAC addresses of internal hosts.
Firewall bypass

A well-crafted HTTP request sent via port 49152 will allow attackers to bypass the modem's internal firewall and open a TCP proxy connection to the device.
Bypassing the firewall allows the attacker to exploit the other four vulnerabilities even if the user thought he secured his router by enabling an on-device firewall.
Arris Pizza Republic Mo Phone Number Lookup
An attacker only needs a modem's public IP address to exploit this bug, but this can be obtained from services like Shodan, Censys, or ZoomEye.
'Every single AT&T device observed has had this port (49152) open and has responded to probes,' Nomotion said.
No exploitation attempts detected yet
The five flaws are not zero-days as researchers have not found any evidence they were exploited in attacks prior to releasing their research.
For owners of said devices, Nomotion has published basic self-mitigation instructions that device owners and ISPs can use to block access to the backdoors and fix some of the flaws. The self-mitigations are available at the end of the Nomotion report.
Victor Gevers, chairman of the GDI Foundation, has also offered his organization's resources in helping users and ISPs mitigate the disclosed issues.
Arris Warranty Lookup
If you are a user or an ISP using these vulnerable Arris devices and you need help fixing the security issues? Then please ping us here. https://t.co/7nPHbHCZ4z
— GDI Foundation (@GDI_FDN) August 31, 2017