| Developer(s) | Salvatore Sanfilippo (Antirez) |
|---|---|
| Stable release | |
| Repository | |
| Written in | C |
| Operating system | Cross-platform |
| Platform | CLI |
| Type | Computer security |
| License | GNU General Public License v2 |
| Website | www.hping.org |
Hping Is A Tool Used To
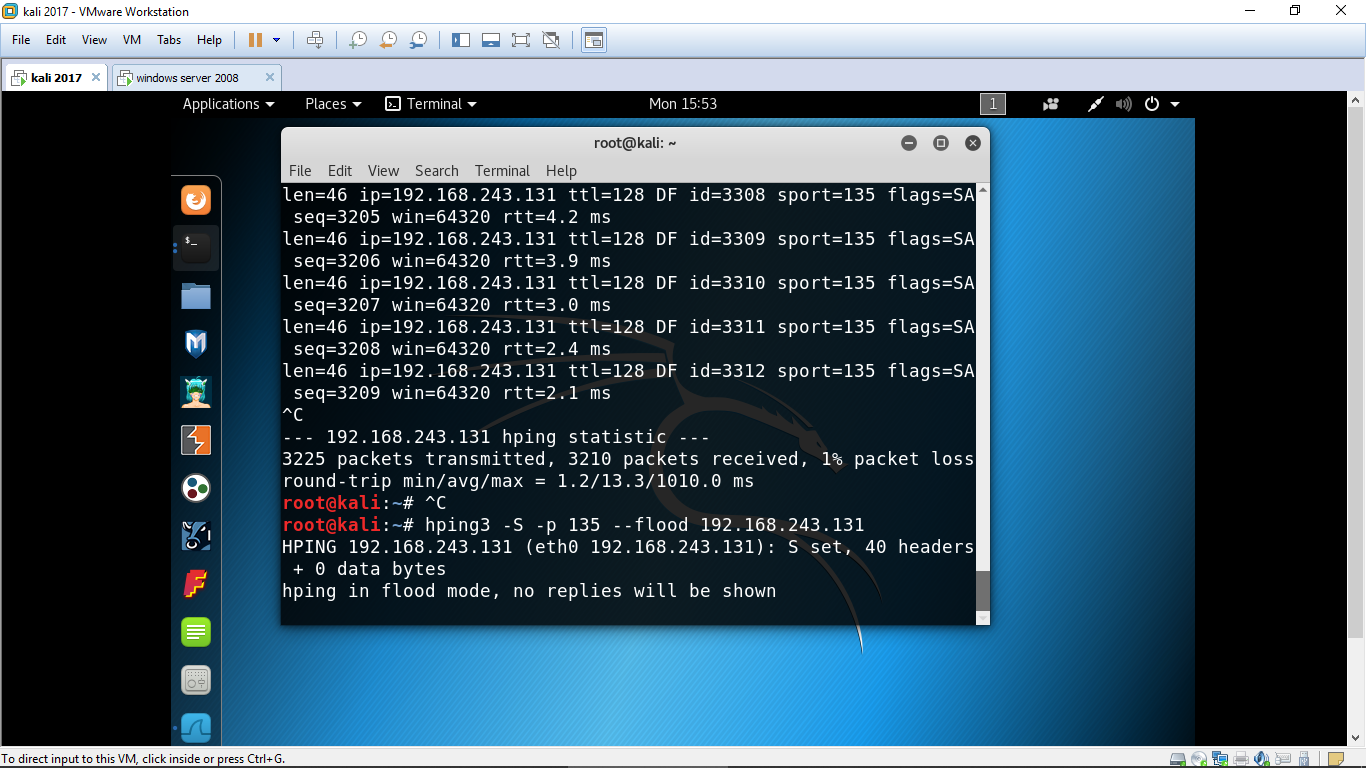
Hping3 README file antirez@invece.org DESCRIPTION hping3 is a network tool able to send custom TCP/IP packets and to display target replies like ping do with ICMP replies. Hping3 can handle fragmentation, and almost arbitrary packet size and content, using the command line interface. Since version 3, hping implements scripting capabilties, read. Apr 21, 2015 hping3 is a free packet generator and analyzer for the TCP/IP protocol. Hping is one of the de-facto tools for security auditing and testing of firewalls and networks, and was used to exploit the Idle Scan scanning technique now implemented in the Nmap port scanner. Package sending with Hping. With the first packet sent with hping, TCP packet exchange is initiated. You can check this inter-flag shopping from that port with the tcpdump program. SYN packet (hping3 -S): It is a TCP connection request. The first connection is initiated with this package. Nping is an open source tool for network packet generation, response analysis and response time measurement. Nping can generate network packets for a wide range of protocols, allowing users full control over protocol headers. While Nping can be used as a simple ping utility to detect active hosts, it can also be used as a raw packet generator. Hping3 is a network tool able to send custom TCP/IP packets and to display target replies like ping program does with ICMP replies. Hping3 handle fragmentation, arbitrary packets body and size and can be used in order to transfer files encapsulated under supported protocols.

hping is an open-source packet generator and analyzer for the TCP/IP protocol created by Salvatore Sanfilippo (also known as Antirez).It is one of the common tools used for security auditing and testing of firewalls and networks, and was used to exploit the idle scan scanning technique (also invented by the hping author), and now implemented in the Nmap Security Scanner. The new version of hping, hping3, is scriptable using the Tcl language and implements an engine for string based, human-readable description of TCP/IP packets so that the programmer can write scripts related to low level TCP/IP packet manipulation and analysis in a short time.

See also[edit]
- Nmap Security Scanner: Nmap and hping are often considered complementary to one another.
- Mausezahn: Another fast and versatile packet generator that also supports Ethernet header manipulation.
- Packet Sender: A packet generator with a focus on ease of use.
External links[edit]
- Idle Scanning, paper by Nmap author Fyodor.

| Port details | |||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||||
|
Number of commits found: 21
Hping Tool
| Commit History - (may be incomplete: see SVNWeb link above for full details) | ||
| Date | By | Description |
|---|---|---|
| 06 Apr 2021 14:31:07 2.0.0r3_2,1 | ||
| 09 Dec 2020 02:30:00 2.0.0r3_2,1 | ||
| 02 Sep 2020 09:38:09 2.0.0r3_2,1 | ||
| 02 Nov 2018 13:32:35 2.0.0r3_2,1 | ||
| 01 Aug 2018 16:33:11 2.0.0r3_2,1 | ||
| 11 Nov 2016 07:21:12 2.0.0r3_2,1 | ||
| 08 Nov 2016 03:45:22 2.0.0r3_2,1 | ||
| 19 May 2016 10:44:12 2.0.0r3_2,1 | ||
| 31 Dec 2015 14:59:34 2.0.0r3_2,1 | ||
| 31 Dec 2015 08:51:18 2.0.0r3_1,1 | ||
| 31 Dec 2015 06:18:46 2.0.0r3_1,1 | ||
| 22 Dec 2015 15:51:01 2.0.0r3_1,1 | ||
| 20 Sep 2015 20:54:09 2.0.0r3,1 | ||
| 22 May 2015 20:34:29 2.0.0r3,1 | ||
| 28 Feb 2014 08:45:12 2.0.0r3,1 | ||
| 20 Sep 2013 22:10:25 2.0.0r3,1 | ||
| 12 Dec 2012 21:40:55 2.0.0r3,1 | ||
| 24 Oct 2011 09:11:38 2.0.0r3,1 | ||
| 20 Mar 2011 12:54:45 2.0.0r3,1 | ||
| 15 Nov 2005 10:30:07 2.0.0r3,1 | ||
| 15 Nov 2005 08:59:45 2.0.0r3,1 | ||
Siping Tool
Number of commits found: 21